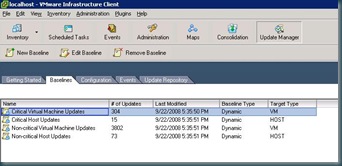
Patching servers or guests using VUM is based on application of baselines. You can apply baselines at any level in the hierarchy of Hosts & Clusters for Host based updates or at any level of the hierarchy of Virtual Machines and Templates for Guest based updates. Baselines can either be static or dynamic, and can be manipulated via the baseline tab of VUM. In the screen shot below it shows the default baselines created by VUM, which are all dynamically updated baselines.
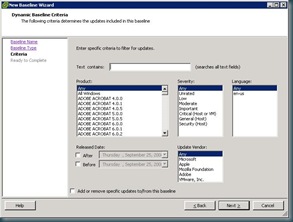
If you choose to create a new baseline you can customize it for Host or Guest Updates, whether the baseline is Fixed or Dynamic. After selecting these criteria, this is where creating a baseline gets interesting. You can select products, update severity, language, date range criteria, and which vendor updates your baseline will include. Currently vendors include VMware, Microsoft, Apple, Mozilla, and Adobe. That is a much larger list than I expected. You can also choose specific updates to include or exclude on subsequent screens.
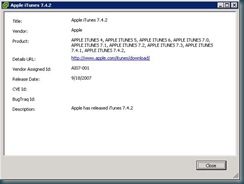
You can also check patch details from the subsequent inclusion/exclusion screen (or from the update repository tab). I chose this update in particular to display, because I was surprised to find in among the included updates.
Now that we have created baselines or used the default baselines, now it is time to attach them. If you want to applying a baseline to an ESX host, you would apply them in the Hosts and Clusters view of the inventory. If you are choosing to apply guest based baselines then you would apply them in the Virtual Machines and Templates. You can apply them at any container level within the hierarchy. I chose to deploy our host based baselines at the datacenter level.
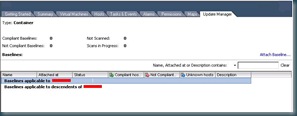
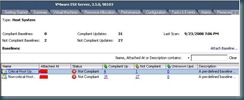
when you attach the baseline you will be asked to select which applicable baseline you wish to apply to the selected container. Once the baseline is applied you will get a view that shows the number of hosts that are compliant with the baseline, the number that are not compliant, and the unknown servers (which have not yet been scanned)
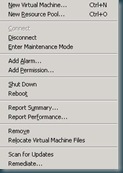
Now from each host (or guest) you will now have additional options in the context menu, Scan for Updates and Remediate.
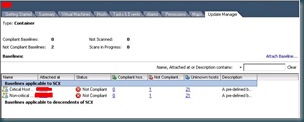
before you scan for updates, make sure that your update repository has already been populated. When I scanned without a populated repository, I received and error stating that the scan could not be completed. You can scan from any level in the hierarchy that has an applied baseline. For the purposes of this blog, I scanned at an individual host level. Once the scan has been completed, you will now see an updated screen showing you the updates compliance status based on your scan.
Now it's time to remediate. clicking remediate will bring up a wizard, asking you to select the baselines that you will be applying. and allows you to select include or exclude updates contained within the baselines. 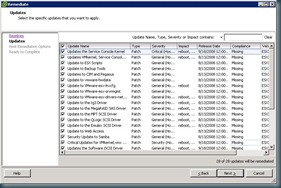
Now you are asked for when you will apply the updates, and you can have an opportunity to adjust the default failure options.
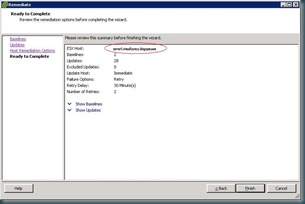
Normally I wouldn't publish a confirmation screen, but there is one specific thing I would like to point out. This is the only place in this wizard where you can see the scope of the update remediation. Since this tool will try to force your servers into maintenance mode, including rebooting servers that are unable to enter maintenance mode (if you have selected that option), it is good to confirm that the scope is limited to what you have intended to patch.
You will now see a task for remediation on the selected hosts, and after it is completed, you will be able to see an event for each patch applied as well as events for entering maintenance mode, and rebooting the server.
In my opinion the time spent configuring VMware Update Manager is time well spent, as it will save much more time in the long run. It's very nice to see VMware follow in the footsteps of Microsoft SUS and WSUS in making a free patch management tool, as opposed to going in the direction of "paid updates" model.





1 comment:
Great Article! Helped out alot! Thanks!
Post a Comment